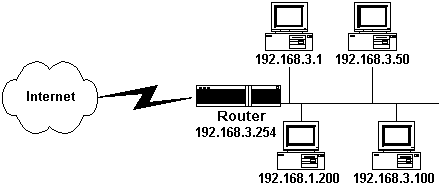
Catching up with TCP/IP fundamentals: IP
address classes
Jim McIntyre
Before
two or more computers can communicate with each other, a set of rules has to be
in place describing the procedures for each host or router on the network to
follow when sending data to—or receiving data from—other hosts or routers. This
set of rules is referred to as a protocol, and TCP/IP is the most common
set of rules in use for computing today. To understand computer networking as
well as internetworking, you must understand the TCP/IP protocol suite. In this
article, I'll provide you with an introduction to the TCP/IP protocol suite.
IP addresses
The TCP/IP protocol suite uses an Internet address, or IP address, to uniquely
identify each host or router on an internetwork. What
makes IP addresses unique is that each address identifies only one host or
router on the Internet. Any host or router that wants to be connected to the
Internet must use the addressing scheme used by TCP/IP.
An IP address is a 32-bit (4-byte) number written in dot notation, which simply
means that each byte is separated by a dot, or period. A typical IP address in
dot notation would look like this:
192.168.10.21
The same address written in binary format would be:
11000000.10101000.00001010.00010101
As you can see from the binary example above, each byte in an IP address can
represent any number from 0 to 255. With 4 bytes used in each IP address, this
means that the total number of IP addresses available is 232, or
4,294,967,296 possible IP addresses. Every IP address contains two distinct
parts:
- The netid identifies
the network.
- The hostid identifies
the host on that network.
IP address classes
Although a lot of IP addresses are available, you don't just pick out any
address for use with your company network and assign addresses however you
like. Depending on your networking requirements, you are assigned (by your
service provider) a specific class of IP address.
There are five classes of IP addresses: A, B, C, D, and E. In the following
sections, I'll discuss each class.
Class A addresses
Class A networks are assigned to organizations with very large numbers of
computers—including servers and routers—attached to their networks. A
government department or a Fortune 500 corporation would be examples of this
type of network. The following characteristics apply to class A networks:
- Class A addresses range from 0.0.0.0 to
127.255.255.255.
- The leftmost bit in a class A network is always
0.
- The first 8 bits (first byte) define the netid.
- The remaining 24 bits define the hostid.
It would
appear that because the first 8 bits define the netid,
the maximum number of class A networks available would
be 27, or 128 networks. However, a netid
with all bits set to 1 and a netid with all bits set
to 0 are reserved for special use. This means that the actual number of class A networks available is 27 minus 2, or 126
networks.
As I mentioned earlier, class A
addresses use 24 bits to define the hostid. In
theory, there is a maximum of 224, or 16,777,216, hostids available. Like netids, a
hostid with all bits set to 1 and a hostid with all bits set to 0 are reserved for special use.
This means that the actual maximum number of hostid
addresses on a class A network is 224 minus
2, or 16,777,214.
This limitation applies to all IP address classes. I'll
discuss the limitation in more detail later.
Class B addresses
Class B networks are also assigned to organizations with large networks. Class
B networks have the following characteristics:
- Class B network addresses range from 128.0.0.0
to 191.255.255.255.
- The first 2 bits in a class B address are always
10 (128).
- In a class B network, the netid
is determined by the first 8 bits (first 2 bytes).
- The hostid is
determined by the last 8 bits (last 2 bytes).
- There are 216 (65,536) possible IP
addresses for each class B network.
- The netids 172.16.0.0
to 173.31.0.0 are reserved for special use. This makes the actual maximum
number of class B netids 216 minus 2,
or 65,534.
Class C addresses
Class C networks are assigned to organizations with small to medium networks.
The class C network is the most common network in use today. Class C networks
have the following characteristics:
- Class C network addresses range from 192.0.0.0
to 223.255.255.255.
- Class C networks use the first 24 bits to
determine the netid.
- The three leftmost bits in a class C network are
always 110 (192).
- The next 21 bits are used to define network.
- There are 216, or 2,097,152, possible
class C networks.
- In class C networks, 8 bits are used to define
the hostid. Because an address with all bits set
to 1 or all bits set to 0 is not allowed, the maximum number of hostids on a class C network is 28 minus 2,
or 254 hostids.
Class D IP addresses
Class D IP addresses are reserved for multicasting. Class D networks have the
following characteristics:
- Class D network addresses range from 224.0.0.0 to
239.255.255.255.
- In class D addresses, the first 4 bits are always 1110
(224).
- The remaining 28 bits are used to define multicast
addresses.
- There is no netid or hostid in a class D address. The whole address is used
for multicasting.
Class
Class E addresses are reserved for special use on the Internet. There is no netid or hostid in a class E
address. Class E network addresses range from 240.0.0.0 to 255.225.225.225. The
first 4 bits in a class address are always 1111 (240).
Determining the address
class
For any given IP address, the address class is easy to determine. If the
address is written in binary format, the leftmost bits in the address will
define the class.
- If the first bit is 0, the address is a class A address.
- If the first bit is 1 and the second bit is 0,
the address is a class B address.
- If the first 2 bits are 1 and the third bit is
0, the address is a class C address.
- If the first 3 bits are 1 and the fourth is 0,
the address is a class D address.
- If the first 4 bits are 1, the address is a
class E address.
- If the address is written in decimal format, the
first number determines the address.
- If the first number is between 0 and 127
inclusive, the address is class A.
- If the first number is between 128 and 191
inclusive, the address is class B.
- If the first number is between 192 and 223
inclusive, the address is class C.
- If the first number is between 224 and 239
inclusive, the address is class D.
- If the first number is between 240 and 255
inclusive, the address is class E.
Determining the netid and hostid
Determining the netid and hostid
contained within any given IP address is not difficult. Once you've determined
the class of the IP address, use the following process:
- If the class is class A, the first byte is the netid and the remaining 3 bytes are the hostid.
- If the class is class B, the first 2 bytes are the netid and the remaining 2 bytes are the hostid.
- For a class C address, the first 3 bytes are the netid and the last byte is the hostid.
- For a class D address, there is no netid
or hostid. All class D addresses are reserved
for multicasting.
- For class E addresses, there is no netid
or hostid. All class E addresses are reserved
for special uses.
The
table below lists the number of netids and hostids available for each IP address class.
|
Class |
Number of
network addresses |
Number of
host addresses |
|
A |
27
- 2 (126) |
224
– 2 (16,777,214) |
|
B |
214
–2 (16,384) |
216
– 2 (65,534) |
|
C |
221
–2 (2,097,152) |
28
– 2 (154) |
|
D |
None |
None |
|
E |
None |
None |
We've listed the number of netids and hostids available for
each IP address class.
Special IP addresses
Classes A, B, and C each have addresses set aside for special purposes. You
should become familiar with six special addresses, which I'll describe in the
following sections.
Network address
In class A, B, and C addresses, any address with a hostid
with all bits set to 0 is used to define the network address. This address is
never assigned to a host. This simply means that your network itself is given
an IP address with all the hostid bits set to 0. This
is not the same as the netid. The network address is
always an address with the host bits set to 0. For example, if a host on a
network has an IP address of 142.23.120.24, the network address is:
142.23.0.0
This host on this network
If an IP address consists of all zeros, the address refers to this host on this
network. A host uses this address when it is booted, but the host does not know
its IP address. This address is always a class A
address, regardless of the network configuration.
Specific host on this network
An IP address with all netid bits set to 0 refers to
a specific host on this network. Setting the netid
bits to 0 ensures that any IP information sent using this address is not
routed. The information will remain within the local network. For example, if
my IP address is 216.120.46.100 and I know I am on the 216.120.46 local
network, I could send information to the host with the IP address 216.120.46.69
by using the address 0.0.0.60.
Direct broadcast address
Any class A, B, or C address with the hostid set to
all ones is known as a direct broadcast address. Routers sending information to
all hosts on a specific network use this address. For example, if you sent IP
information to 204.36.120.255, all hosts on the 204.36.120.0 network would
receive the information sent.
Limited broadcast address
Any class A, B, or C address with all bits set to 1 (255.255.255.255) is used
to send information to all other hosts on the same network as the host sending
the information. In other words, this address sends IP information to all hosts
on your local network.
Loopback address
Any IP address with the first byte set to 127 is used for the loopback address. The loopback
address is used to test the TCP/IP software on a computer; it does not provide
any information on the configuration of a network interface. The most common loopback address is 127.0.0.1. When you run the command
ping 127.0.0.1
you can determine whether your TCP/IP software is running properly. A child
process on a computer may also use the loopback
address to send a message to its parent process.
Private IP networks
There are three blocks of IP addresses that may be used by any organization for
TCP/IP networking. These IP addresses are nonroutable,
meaning they are limited to use within the local network only. The three groups
of nonroutable IP addresses are listed in the table
below.
|
Address
Block |
Netmask |
Class |
|
10.x.x.x |
255.255.255.0 |
A |
|
176.16.0.0/12
–176.31.255.255 |
255.255.0.0 |
B |
|
192.168.0.0
– 192.168.255.0 |
255.255.255.0 |
C |
The three groups of nonroutable IP addresses are shown according to class.
Any organization may use any address from the blocks listed
above without registering the IP addresses used on its network.
Summary
The TCP/IP protocol suite provides the foundation for internetworking. In this
article, I introduced you to the TCP/IP protocol suite.
Getting to know your IP addresses
Todd Lammle
The
Internet Protocol (IP) was developed in the 1960s to provide packet
fragmentation and reassembly across a packet-switched network. This
packet-switched network became what we now call the Internet.
IP addressing is used to uniquely identify hosts on an internetwork. An internetwork is
made of LANs and WANs that are connected with a router or routers. To send data
from a host on network A to a host on network B, a logical network addressing
protocol must be used. IP is the most popular logical addressing protocol.
However, IPX in the Novell stack and Datagram Delivery Protocol (DDP) in the
AppleTalk stack can also be used. Although you can find many other types of
routed protocols that provide the same functionality as IP, in larger networks
they aren't as efficient as IP.
The dreaded IP address
Before we conquer IP addresses, I want to define some of the terminology used
in this article:
- Bit: One digit; either one or zero.
- Byte: 8 bits. This term is interchangeable with octet.
- Octet: 8 bits. This term is interchangeable with byte.
- Network address: Address with all host bits turned off.
- Broadcast address: Address with all host bits turned
on.
To fully
understand IP addressing, you must be familiar with binary-to-decimal
conversion. To find the decimal equivalent of a binary number, you must add the
binary values. Binary numbers use eight bits to create a byte. Each bit in the
byte has a certain value, and if a bit is turned on (assigned a value of 1),
then the byte takes on that decimal value. Each bit has a value that starts at
1 and doubles in value from right to left. Table 1 shows an example of
converting a byte to a decimal value.
|
Table 1 |
||||||||
|
128 |
64 |
32 |
16 |
8 |
4 |
2 |
1 |
Decimal
value |
|
0 |
0 |
0 |
1 |
1 |
0 |
1 |
0 |
Binary
number |
This table shows an example of converting
a byte to a decimal.
In the above example, there are three bits that are turned
on (1s). Add each of these values to get the bytes decimal value (16+8+2=26).
Let's take a look at another example in Table 2.
|
Table 2 |
||||||||
|
128 |
64 |
32 |
16 |
8 |
4 |
2 |
1 |
Decimal
value |
|
0 |
1 |
1 |
0 |
1 |
0 |
0 |
0 |
Binary
number |
In the above example, there are three
bytes that are turned on (64+32+8=104).
The IP address
IP addressing is not hard-coded into a machine. It is known as a software or
logical address because of the way an administrator must statically configure
each host (either manually or with DHCP). The basic design of an IP address
allows hosts on different networks to communicate with each other, regardless
of the type of network on which they are located.
The IP address is 32 bits long and is divided into dotted decimal. An example
of an IP address is: 10.205.34.2. Each of the decimals is known as a
byte and is 8 bits long. Therefore, an IP address is 4 bytes, or 32 bits long.
An IP address is hierarchal in design and is divided into two parts: network
and host. An IP address not only defines the host on the internetwork
but also describes the network on which the host is located. In the example
above, 10 is the network and 205.34.2 is the host address.
The job of a router is to get packets to a network using the logical address.
To get a packet to a host, the hardware address is used. If a packet has a
destination IP address of 10.205.34.2, the routers in the internetwork
will forward the packet to network 10. If the routing tables do not have an
entry for network 10, the routers will discard the packet.
An IP address can only be configured within certain ranges. Although an IP
address can be displayed in decimal from 0.0.0.0 to 255.255.255.255, only
certain addresses can be used to configure hosts on an internetwork.
It is imperative that you can look at an IP address and know whether it's a
valid host address.
Classes of IP addresses
The original designers of the IP stack came up with a hierarchical addressing
scheme with five ranges, called classes. These ranges are named:
- Class A: IP address range from 0-127 in the first byte
designed for very large companies.
- Class B: IP address range from
128-191 in the first byte designed for medium-size companies.
- Class C: IP address range from
192-223 in the first byte designed for small companies.
- Class D: IP address range from 224-239 in the first
byte reserved for multicast addressing. Not used in the public sector.
- Class E: IP address range from
240-255 in the first byte reserved for scientific studies. Not used in the
public sector.
Class A
In the four-byte Class A IP address, only the first
byte is used to identify the network. The last three bytes are used to describe
the hosts on each network: network.host.host.host.
The Class A range is 0-127 in the first byte. Only 1-126 can be used to
identify Class A networks because 0 and 127 are reserved.
To find the valid host addresses in a Class A network,
you must find the network and broadcast address in the IP range. Since the
Class A address only uses the first byte to identify the network, the last
three octets are host bits.
To find the network and broadcast address, turn off the host bits and then turn
them on again. For example, if we want to use the Class A network address of
10, the network address, broadcast address, and valid hosts are determined as
shown:
- 10.0.0.0 is the network
address because all of the host bits are turned off (0). The last three
octets are zeros because the first octet is a 10, which is in the Class A range of 1-126.
- To find the broadcast address of the IP address, turn
on the host bits: 10.255.255.255.
- The valid hosts are the numbers in between the network
address and the broadcast address: 10.0.0.1 through 10.255.255.254.
Class B
The Class B range is 128-191. For example, if you find an IP address that
begins with 152, then you know that it's a Class B address. Class B addresses use the first two bytes to define the network and the last
two bytes to define the hosts on each network: network.network.host.host.
For example, in the IP address 152.93.10.5, 152.93 is the network address and
10.5 is the host address. In this example, what are the network address,
broadcast address, and valid host range? Remember, all you have to do is to find
the host bits and turn them all off and then turn them all on. In a Class B
address, the host bits are the third and fourth octets by default.
- 152.93.0.0 is the network
address (all host bits off).
- 152.93.0.1 is the first valid
host.
- 152.93.255.254 is the last valid host.
- 152.93.255.255 is the broadcast address (all host bits
on).
Class C
In a Class C IP address, only the fourth octet is used to address hosts. The
first three octets are used to define the network: network.network.network.host.
An example of a Class C address is 200.10.10.59. By glancing at this address,
you can see that the network address is 200.10.10 and the host address is 59.
To find the valid host range, turn all of the host bits off and then turn them
on.
- 200.10.10.0 is the network
address because all host bits are off.
- 200.10.10.1 is the first valid
host.
- 200.10.10.254 is the last valid host.
- 200.10.10.255 is the broadcast address because all host
bits are on.
Subnet masks
Subnet masks are used in IP configurations to tell hosts on the network which
part is the network address and which part is the host address of an IP
address. You cannot configure an IP address on a host without also configuring
the subnet mask information.
Remember that a Class A IP address uses only the first
byte to describe the network address and three bytes to describe the host
addresses. In a subnet mask, the network portion consists of all ones (1s) and
the host portion is all zeros (0s). Therefore, a default Class A subnet mask
must be 255.0.0.0. Since the entire first byte is the network portion and must
be all 1s, the decimal value is 255. IP will examine this mask to determine the
host and network bits in an address.
In a Class B IP address, the first two bytes represent the network portion and
the last two bytes are the host portion. Therefore, the default mask is
255.255.0.0.
In a Class C IP address, the first three bytes represent the network portion
and the last byte is the host portion. The default mask is 255.255.255.0.
This is an example of a Class A configuration of a host where 10 is the network
address and 59.135.4 is the host address:
10.59.135.4
255.0.0.0
This is an example of a Class B configuration of a host where 130.59 is the
network address and 135.4 is the host address:
130.59.135.4
255.255.0.0
Here is an example of a Class C configuration of a host where 210.59.135 is the
network address and 4 is the host address:
210.59.135.4
255.255.255.0
The default gateway address is typically configured but is not required. It is
the router address on the network. If no default gateway address is configured
on the host, the host won't be able to communicate outside its own local
network.
Conclusion
In today's computing age, IP addressing is critical in every network. To become
certified in any network program, you must have a fundamental understanding of
IP addressing. If you want a networking job, it's imperative that you're
familiar with IP addressing. You should be able to determine a valid IP address
just by glancing at the IP address and mask. To do this, you must be able to
quickly and efficiently determine the network and broadcast addresses.
![]()
Using variable-length subnetting
with TCP/IP networks
Jim McIntyre
The
process of subnetting large networks is often
restricted by the network mask (netmask) employed.
Quite often, we are required to create several subnetworks,
each with a different number of host computers (workstations). Problems like
this are often solved using variable-length subnetting.
With variable-length subnetting, the administrator
uses two or more subnet masks and each mask is a different length. In this
article, we will look at how variable subnetting may
be used to solve some typical subnetting problems.
Subnetting and subnet masking
Subnetting is the process of dividing a network into
smaller subnetworks, each with its own subnetwork address.
When a network needs to be subnetted, there must be a
way to determine which network an IP address belongs to. Let's assume a
workstation with the IP address 192.168.1.21 is located on the 192.168.1.0
network and wants to send an IP packet to a workstation with the address
192.168.1.130. The computer on the 192.168.1.0 network needs to know if
192.168.1.130 is on the same network or if the IP packet needs to be sent to
the router, where it will be forwarded to another network.
The subnet mask is used to determine whether or not this IP packet belongs to
the local network.
Subnet masking is a process used to extract the physical network address from
an IP address. Actually, masking may be done whether there is a subnet in place
or not. If there is no subnet, masking extracts the network address. If there
is a subnet, masking extracts the subnetwork address.
The problem with subnet masking is that all of the subnets created are the same
size. Subnet masking works well if the administrator needs to create several subnetworks with the same number of hosts on each subnet,
but problems can arise when the number of hosts on each subnet is different.
Variable-length masking provides administrators with an efficient way to create
these subnets.
Variable-length subnet
masking
Due to the rapid growth of the Internet, the number of available IP addresses
is quickly being depleted. This is due to both the number of new networks and
because IP addresses are often assigned to organizations where they are
inefficiently used. For example, an organization might be assigned an entire
block of more than 65,000 class B IP addresses when
addresses are required for only 500 hosts.
To solve this problem, variable-length subnet masks (VLSMs)
were developed. VLSMs allow network and subnetwork identifiers (netid and
subnetid). By using VLSMs,
administrators are able to build flexibility into their IP addressing systems
and are able to assign IP addresses in a more efficient manner.
Let's look at a typical situation a network administrator might have to deal
with. In this example, the administrator is granted a Class C TCP/IP network
address, 192.168.3.0. From this initial address, the organization needs four
subnets created; three of the subnets will have 50 hosts each and two will have
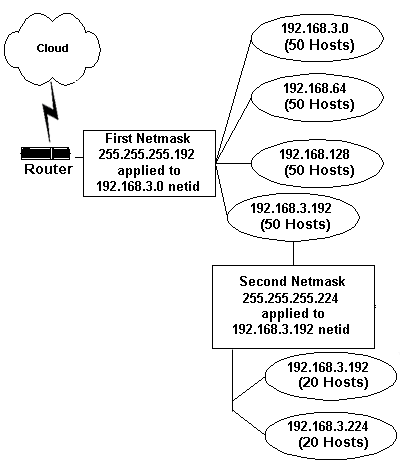
20 hosts each. The original Class C network is shown in Figure A.
|
Figure
A |
|
|
|
Our
original 192.168.3.0 Class C network can quickly become limiting. |
The administrator must first consider which subnet masks
will work in this situation. The best approach here is to look at the
limitations of Class C subnet masks. The limitations include:
- If the standard Class C netmask of 255.255.255.0 is used, only one network is possible, with a maximum of 256 hosts. Using this mask eliminates any subnets.
- If the mask 255.255.255.128 is used, only one
subnet with a maximum of 128 hosts is possible.
- Using two bits in the subnetid
section of the IP address, 255.255.255.192, allows four subnets, each with
a maximum of 62 hosts (256 / 4 – 2 = 62). Sixty-two hosts are more than we
will have on any one subnet, but this allows for only four subnets. The
situation requires five subnets.
- The next subnet mask, 255.255.255.224, allows
for eight subnets to be created, but each subnet is limited to 30 hosts
(256 / 8 =32, and 32 –2 = 30).
The
solution is to use variable-length subnetting. When
variable-length subnetting is employed, the router is
supplied with two subnet masks. These masks are applied one after the other. In
this situation, the administrator first creates four subnets using the mask
255.255.255.192. The original subnet mask is 255.255.255.0, written in binary
as:
11111111.11111111.11111111.00000000
= 255.255.255.0
and the original network IP address was 192.168.3.0, written
in binary as:
11000000.10101000.00000011.00000000
= 192.168.3.0
Now, by applying the new subnet mask of 255.255.255.192,
written in binary as:
11111111.11111111.11111111.11000000
we have added two bits to the network identifier section (netid) of the original IP address. This allows the
administrator to create up to four (22) subnetworks
from the original network address. Each of these newly created subnets may hold
up to 64 (26) hosts.
Once the new subnet mask is determined, the administrator
uses the following to create the subnets required:
- The first step is to apply the mask to the original
192.168.3.0 network address. This new mask creates four new subnetworks (subnets). The subnetwork
identifiers (subnetid) available to the
administrator are:
192.168.3.0
192.168.3.64
192.168.3.128
192.168.3.192
Three of the new subnetworks will each contain 60 hosts. When these first three subnetworks are created, our original Class C network, 192.168.3.0, looks like the example in Figure A. - To create two more subnets, a second subnet mask of
255.255.255.224 is applied. This divides the remaining subnet into two
separate subnets. With five bits remaining to be used as host identifiers
(hostids), each of these new subnets may hold up
to 32 (25) hosts. Once this step is completed, the network now
takes on the configuration shown in Figure B.
|
Figure
B |
|
|
|
Here's our
original 192.168.3.0 network subnetted with two subnet
masks. |
With that step completed, we have now solved our original
problem of how to create five subnetworks with 50
hosts on three of the subnets and 20 hosts on the two subnetworks
created using variable-length subnet masking.
Conclusion
The rapid growth of the Internet has led to many situations where Class C
network addresses are the only ones available to administrators. The ability to
create subnetworks using the procedures outlined in
this article will allow administrators more flexibility in how solutions are
applied to some common networking problems.
Subnetting a Class C network address
Todd Lammle
Let's
face it, some day you are going to have to subnet a network. Although IP
addressing isn't a network administrator's favorite task, it's a critical skill
that you must have. In this article, I will explore the process of taking a
large IP address range and dividing it into smaller, more manageable pieces.
Since this is a complicated, involved process, I will only discuss the process
of breaking up Class C networks. First, however, I need to discuss why you'd
want to subnet a network and the advantages of doing so.
Why subnetting?
By creating smaller IP networks (instead of having one large network), you can
obtain better security, smaller collision and broadcast domains, and greater
administrative control of each network. Think of a network like streets in a
city. Each house on this network is known by the street and by the address.
Think of the addresses on the houses as the hardware addresses of a host. For
IP to communicate with a host, the IP address must be known, and the router
connected to the network on which this host is located must also know the
hardware address of the house.
What if a city didn't have many blocks but just one long street? The mail
carriers would go crazy trying to get the mail delivered to each house
correctly because they would have to know the address of every house. It's the
same scenario with IP. By creating smaller networks, you can more effectively
get data to each host.
Subnetting a Class C network
So you understand why you want to subnet, but how do you do it? Your goal is to
look at an IP address and subnet mask of a host and then determine three things
quickly:
- The subnet the
host is located in
- The broadcast
address of the subnet
- The valid host
range of the subnet used to configure hosts
Once the subnet is determined, the broadcast address must
be found. Why? Because these are not valid host addresses and cannot be
assigned to host configurations. Also, by determining the subnet and broadcast
addresses, you can easily determine the host addresses because the valid host
range is always the numbers between the subnet address and the broadcast
address.
If you use the default subnet mask with a Class C network
address, then you already know that three bytes are used to define the network
and only one byte is used to define the hosts on each network.
The default Class C mask is: 255.255.255.0. To make
smaller networks, called subnetworks, you will borrow
bits from the host portion of the mask. Since the Class C mask only uses the
last octet for host addressing, you only have 8 bits at your disposal.
Therefore, only the following masks can be used with Class C networks (Table
A).
|
Table A |
|||||
|
Mask |
Binary |
# Subnet bits |
# Host bits |
Subnets |
Hosts |
|
255.255.255.128 |
10000000 |
1 |
7 |
2 |
126 |
|
255.255.255.192 |
11000000 |
2 |
6 |
2 |
62 |
|
255.255.255.224 |
11100000 |
3 |
5 |
6 |
30 |
|
255.255.255.240 |
11110000 |
4 |
4 |
14 |
14 |
|
255.255.255.248 |
11111000 |
5 |
3 |
30 |
6 |
|
255.255.255.252 |
11111100 |
6 |
2 |
62 |
2 |
Class C masks
You can see in Table A that the bits that are turned on
(1s) are used for subnetting, while the bits that are
turned off (0s) are used for addressing of hosts. You can use some easy math to
determine the number of subnets and hosts per subnet for each different mask.
To determine the number of subnets, use the 2x-2,
where the x exponent is the number of subnet bits in the mask.
To determine the number of hosts, use the 2x-2,
where the x exponent is the number of host bits in the mask.
To determine the mask you need for your network, you must
first determine your business requirements. Count the number of networks and
the number of hosts per network that you need. Then determine the mask by using
the equations shown above—and don't forget to factor for growth.
For example, if you have eight networks and each requires
10 hosts, you would use the Class C mask of 255.255.255.240. Why? Because 240
in binary is 11110000, which means you have four subnet bits and four host
bits. Using this math, you'd get the following:
24-2=14 subnets
24-2=14 hosts
Many people find it easy to memorize the Class C
information because Class C networks have few bits to manipulate. However,
there is an easier way to subnet.
Easy subnetting
Instead of memorizing the entire table (Table A), it's possible to glance at a
host address and quickly determine the necessary information if you've
memorized key parts of the table. First, you need to know your
binary-to-decimal conversion. Memorize the number of bits used with each mask
that are shown in Table A. Second, you need to remember the following:
256-192=64
256-224=32
256-240=16
256-248=8
256-252=4
Once you have the two steps memorized, you can begin subnetting.
Our first example will use the Class C mask of 255.255.255.192. Ask five simple
questions to gather all the facts:
- How many
subnet bits are used in this mask?
- How many host
bits are available per subnet?
- What are the
subnet addresses?
- What is the
broadcast address of each subnet?
- What is the
valid host range of each subnet?
You already know how to answer questions one and two. To
answer question three, use the formula 256-subnetmask to get the first
subnet and your variable. Keep adding this number to itself
until you get to the subnet mask value to determine the valid subnets. Once you
verify all of the subnets, you can determine the broadcast address by looking
at the next subnet's value. The broadcast address is the number just before the
next subnet number. Once you have the subnet number and broadcast address, the
valid hosts are the numbers in between.
Here are the answers using 255.255.255.192:
- How many
subnet bits are used in this mask?
Answer: 2
22-2=2 subnets - How many host
bits are available per subnet?
Answer: 6
26-2=62 hosts per subnet - What are the
subnet addresses?
Answer: 256-192=64 (the first subnet)
64+64=128 (the second subnet)
64+128=192. However, although 192 is the subnet mask value, it's not a valid subnet. The valid subnets are 64 and 128. - What is the
broadcast address of each subnet?
Answer: 64 is the first subnet and 128 is the second subnet. The broadcast address is always the number before the next subnet. The broadcast address of the 64 subnet is 127. The broadcast address of the 128 subnet is 191. - What is the
valid host range of each subnet?
Answer: The valid hosts are the numbers between the subnet number and the mask. For the 64 subnet, the valid host range is 64-126. For the 128 subnet, the valid host range is 129-190.
Let's do a second example using the Class C mask of
255.255.255.224. Here are the answers:
- How many
subnet bits are used in this mask?
Answer: 3 bits or 23-2=6 subnets - How many host
bits are available per subnet?
Answer: 5 bits or 25-2=30 hosts per subnet - What are the
subnet addresses?
Answer: 256-224 =32, 64, 96, 128, 160 and 192 (Six subnets found by continuing to add 32 to itself.) - What is the
broadcast address of each subnet?
Answer: The broadcast address for the 32 subnet is 63. The broadcast address for the 64 subnet is 95. The broadcast address for the 96 subnet is 127. The broadcast address for the 160 subnet is 191. The broadcast address for the 192 subnet is 223 (since 224 is the mask). - What is the
valid host range of each subnet?
Answer: The valid hosts are the numbers in between the subnet and broadcast addresses. For example, the 32 subnet valid hosts are 33-62.
Let's do a third example using the Class C mask of
255.255.255.240. Here are the answers:
- How many
subnet bits are used in this mask?
Answer: 4 bits or 24-2=14 subnets - How many host
bits are available per subnet?
Answer: 4 bits or 24-2=14 hosts per subnet - What are the
subnet addresses?
Answer: 256-240 =16, 32, 48, 64, 80, 96, 112, 128, 144, 160, 176, 192, 208, and 224 (14 subnets found by continuing to add 16 to itself). - What is the
broadcast address of each subnet?
Answer: Here are some examples of the broadcast address: The broadcast address for the 16 subnet is 31. The broadcast address for the 32 subnet is 47. The broadcast address for the 64 subnet is 79. The broadcast address for the 96 subnet is 111. The broadcast address for the 160 subnet is 175. The broadcast address for the 192 subnet is 207. - What is the
valid host range of each subnet?
Answer: The valid hosts are the numbers in between the subnet and broadcast addresses. The 32 subnet valid hosts are 33-46.
Let's do a fourth example using the Class C mask of
255.255.255.248. Here are the answers:
- How many
subnet bits are used in this mask?
Answer: 5 bits or 25-2=30 subnets - How many host
bits are available per subnet?
Answer: 3 bits or 23-2=6 hosts per subnet - What are the
subnet addresses?
Answer 256-248 =8, 16, 24, 32, 40, 48, and so forth. The last subnet is 240 (30 subnets found by continuing to add 8 to itself). - What is the
broadcast address of each subnet?
Answer: The broadcast address for the 8 subnet is 15. The broadcast address for the 16 subnet is 23. The broadcast address for the 48 subnet is 55. - What is the
valid host range of each subnet?
Answer: The valid hosts are the numbers in between the subnet and broadcast addresses. For example, the 32 subnet valid hosts are 33-38.
Let's do a fifth example using the Class C mask of
255.255.255.252. Here are the answers:
- How many subnet bits are used in this mask?
Answer: 6 bits or 26-2=62 subnets - How many host bits are available per subnet?
Answer: 2 bits or 22-2=2 hosts per subnet - What are the subnet addresses?
Answer: 256-252 =4, 8, 12, 16, 20, and so forth. The last subnet is 248 (62 subnets found by continuing to add 4 to itself). - What is the broadcast address of each subnet?
Answer: The broadcast address for the 4 subnet is 7. The broadcast address for the 8 subnet is 11. The broadcast address for the 12 subnet is 15. The broadcast address for the 20 subnet is 23. - What is the valid host range of each subnet?
Answer: The valid hosts are the numbers in between the subnet and broadcast addresses. For example, the 16 subnet valid hosts are 17 and 18.
How do I use this
information?
Let's take a look at an example that will highlight how the above information
is applied.
A host configuration has an IP configuration of 192.168.10.17 255.255.255.248.
What are the subnet, broadcast address, and host range that this host is a
member of? The answer is: 256-248=8, 16, 24. This host
is in the 16 subnet, the broadcast address of the 16 subnet is 23, and the
valid host range is 17-22. Pretty easy!
Here is an explanation of this example: First, I used 256-subnetmask to get the
variable and first subnet. Then this number was repeatedly added to itself
until the host address was passed. The subnet is the number before the host
address, and the broadcast address is the number right before the next subnet.
The valid hosts are the numbers in between the subnet and broadcast address.
Let's examine a second example. A host configuration has an IP configuration of
192.168.10.37 255.255.255.240. What are the subnet,
broadcast address, and host range this host is a member of? The answer is:
256-240=16, 32, 48. This host is in the 32 subnet, the
broadcast address of the 32 subnet is 47, and the valid host range is 33-46.
Let's go through a third example: A host configuration has an IP configuration
of 192.168.10.44 255.255.255.224. What are the subnet,
broadcast address, and host range this host is a member of? The answer is:
256-224=32, 64. This host is in the 32 subnet, the broadcast address of the 32
subnet is 63, and the valid host range is 33-62.
Here's a fourth example: A host configuration has an IP configuration of
192.168.10.17 255.255.255.252. What are the subnet,
broadcast address, and host range this host is a member of? The answer is:
256-252=4, 8, 12, 16, 20. This host is in the 16
subnet, the broadcast address of the 16 subnet is 19, and the valid host range
is 17-18.
Let's go through a final example. A host configuration has an IP configuration
of 192.168.10.88 255.255.255.192. What are the subnet, broadcast address and
host range this host is a member of? The answer is: 256-192=64, 128. This host
is in the 64 subnet, the broadcast address of the 64 subnet is 128, and the
valid host range must be 65-126.
Conclusion
It is important to be able to subnet quickly and efficiently. After studying
the examples presented in this article, you should be familiar with this
process with Class C addresses. Practice your subnetting as much as possible, and the process will get
easier and easier.
Class B subnets
As you know, Class C network addresses only have eight bits to manipulate into
subnets. However, a Class B address has 16 bits to play with. This will allow more
subnets with more hosts per subnet than a Class C network ever could.
Table 1 lists all of the possible Class B subnets:
|
Table 1 |
|||
|
Mask |
Binary |
Subnets |
Hosts per
subnet |
|
255.255.128.0 |
10000000.00000000 |
2 |
32,766 |
|
255.255.192.0 |
11000000.00000000 |
2 |
16,382 |
|
255.255.224.0 |
11100000.00000000 |
6 |
8,190 |
|
255.255.240.0 |
11110000.00000000 |
14 |
4,094 |
|
255.255.248.0 |
11111000.00000000 |
30 |
2,046 |
|
255.255.252.0 |
11111100.00000000 |
62 |
1,022 |
|
255.255.254.0 |
11111110.00000000 |
126 |
510 |
|
255.255.255.0 |
11111111.00000000 |
254 |
254 |
|
255.255.255.128 |
11111111.10000000 |
510 |
126 |
|
255.255.255.192 |
11111111.11000000 |
1022 |
62 |
|
255.255.255.224 |
11111111.11100000 |
2,046 |
30 |
|
255.255.255.240 |
11111111.11110000 |
4,094 |
14 |
|
255.255.255.248 |
11111111.11111000 |
8,190 |
6 |
|
255.255.255.252 |
11111111.11111100 |
16,382 |
2 |
All possible Class B subnets
There are quite a few more masks we can use with a Class B
network address than we can with a Class C network address. Remember that this
is not harder than subnetting with Class C, but it
can get confusing if you don't pay attention to where the subnet bits and host
bits are in a mask. This takes practice!
In this article, we will use the same techniques we used
in "Subnetting a Class C network address" to subnet a
network. We'll start with the Class B subnet mask of 255.255.192.0 and figure
out the subnets, broadcast address, and valid host range. You will need to
answer the same five questions that you answered for the Class C subnet masks:
- How many subnets does this mask provide?
- How many hosts per subnet does this mask
provide?
- What are the valid subnets?
- What is the broadcast address for each subnet?
- What is the host range of each subnet?
Before answering these questions, there is one difference
you need to be aware of when subnetting a Class B
network address. When subnetting in the third octet,
you need to add the fourth octet. For example, on the 255.255.192.0 mask, the subnetting will be done in the third octet. To create a
valid subnet, you must add the fourth octet of all 0s and all 1s for the
network and broadcast address (0 for all 0s and 255 for all 1s).
Example 1: Answers for the 255.255.192.0 mask
- 22-2=2 subnets
- 214-2=16,382 hosts per subnet
- 256-192=64.0, 128.0
- Broadcast for the 64.0 subnet is 127.255. Broadcast for
the 128.0 subnet is 191.255.
- The valid hosts are:
|
Subnet |
64.0 |
128.0 |
|
first
host |
64.1 |
128.1 |
|
last host |
127.254 |
191.254 |
|
broadcast |
127.255 |
191.255 |
Notice that the numbers in the third octet are the same numbers
you used in the fourth octet when subnetting the 192
mask. The only difference is that you add 0 and 255 in the fourth octet.
For the 64.0 subnet, all the hosts between 64.1 and
127.254 are in the 64 subnet. In the 128.0 subnet, the hosts are 128.1 through
191.254.
Work through a few more with me, and it should start to
become clearer.
Example 2: 255.255.240.0
- 24-2=14 subnets
- 212-2=4,094 hosts per subnet
- 256-240=16.0, 32.0, 48.0, 64.0, etc.
- Broadcast for the 16.0 subnet is 31.255. Broadcast for
the 32.0 subnet is 47.255, etc.
- The valid hosts are:
|
Subnet |
16.0 |
32.0 |
48.0 |
64.0 |
|
first
host |
16.1 |
32.1 |
48.1 |
64.1 |
|
last host |
31.254 |
47.254 |
63.254 |
79.254 |
|
broadcast |
31.255 |
47.255 |
63.255 |
79.255 |
Example 3: 255.255.248.0
- 25-2=30 subnets
- 211-2=2,046 hosts per subnet
- 256-248=8.0, 16.0, 24.0, 32.0, 40.0, 48.0, 56.0,
64.0, etc.
- Broadcast for the 8.0 subnet is 15.255.
Broadcast for the 16.0 subnet is 23.255, etc.
- The valid hosts are:
|
Subnet |
8.0 |
16.0 |
24.0 |
32.0 |
40.0 |
48.0 |
56.0 |
64.0 |
|
first
host |
8.1 |
16.1 |
24.1 |
32.1 |
40.1 |
48.1 |
56.1 |
64.1 |
|
last host |
15.254 |
23.254 |
31.254 |
39.254 |
47.254 |
55.254 |
63.254 |
71.254 |
|
broadcast |
15.255 |
23.255 |
31.255 |
39.255 |
47.255 |
55.255 |
63.255 |
71.255 |
Example 4: 255.255.252.0
- 26-2=62 subnets
- 210-2=1,022 hosts per subnet
- 256-252=4.0, 8.0, 12.0, 16.0, 20.0, 24.0, 28.0,
32.0, etc.
- Broadcast for the 4.0 subnet is 7.255. Broadcast
for the 8.0 subnet is 11.255, etc.
- The valid hosts are:
|
Subnet |
4.0 |
8.0 |
12.0 |
16.0 |
20.0 |
24.0 |
28.0 |
32.0 |
|
first
host |
4.1 |
8.1 |
12.1 |
16.1 |
20.1 |
24.1 |
28.1 |
32.1 |
|
last host |
7.254 |
11.254 |
15.254 |
19.254 |
23.254 |
27.254 |
31.254 |
35.254 |
|
broadcast |
7.255 |
11.255 |
15.255 |
19.255 |
23.255 |
27.255 |
31.255 |
35.255 |
Example 5: 255.255.255.0
- 28-2=254 subnets
- 28-2=254 hosts per subnet
- 256-255=1.0, 2.0, 3.0, 4.0, 5.0, 6.0, 7.0, 8.0,
etc.
- Broadcast for the 1.0 subnet is 1.255. Broadcast
for the 2.0 subnet is 2.255, etc.
- The valid hosts are:
|
Subnet |
1.0 |
2.0 |
3.0 |
4.0 |
5.0 |
6.0 |
7.0 |
8.0 |
|
first
host |
1.1 |
2.1 |
3.1 |
4.1 |
5.1 |
6.1 |
7.1 |
8.1 |
|
last host |
1.254 |
21.254 |
3.254 |
4.254 |
5.254 |
6.254 |
7.254 |
8.254 |
|
broadcast |
1.255 |
2.255 |
3.255 |
4.255 |
5.255 |
6.255 |
7.255 |
8.255 |
That last example was pretty simple. You should notice a
pattern now. All the numbers were basically the same except we added the fourth
octet into the address.
The more difficult process of subnetting
a Class B network address is when you start using bits in the fourth octet for subnetting. For example, what happens when you use this
mask with a Class B network address: 255.255.255.128? Is that valid?
Absolutely! There are nine bits for subnetting and
seven bits for hosts. That is 510 subnets, each with 126 hosts. However, it is
the most difficult mask to figure out the valid hosts for.
Example 6: The Class B 255.255.255.128 subnet mask:
- 29-2=510 subnets
- 27-2=126 hosts per subnet
- For the third octet, the mask would be 256-255=1, 2, 3,
4, 5, 6, etc.
- For the fourth octet, the mask would be 256-128=128,
which is one subnet if it is used. However, if you turn the subnet bit
off, the value is 0. This means that for every subnet in the third octet,
the fourth octet has two subnets: 0 and 128, for example 1.0 and 1.128.
- Broadcast for the 0.128 subnet is 128.255; the
broadcast for the 1.0 subnet is 1.127. Broadcast for the 1.128 subnet is
1.255, etc.
- The valid hosts are:
|
Subnet |
0.128 |
1.0 |
1.128 |
2.0 |
2.128 |
3.0 |
3.128 |
4.0 |
|
first
host |
0.129 |
1.1 |
1.129 |
2.1 |
2.129 |
3.1 |
3.129 |
4.1 |
|
last host |
0.254 |
1.126 |
1.254 |
2.126 |
2.254 |
3.126 |
3.254 |
4.126 |
|
broadcast |
0.255 |
1.127 |
1.255 |
2.127 |
2.255 |
3.127 |
3.255 |
4.127 |
The thing to remember is that for every subnet in the
third octet, there are two in the fourth octet: 0 and 128. For the 0 subnet,
the broadcast address is always 127. For the 128 subnet, the broadcast address
is always 255.
Let's continue with more subnetting
into the fourth octet. This is exactly like subnetting
a Class C network address, but the third octet is part of the subnet address.
Example 7: Class B network 255.255.255.192
- 210-2=1,022 subnets
- 26-2=62 hosts per subnet
- 256-255=1.0, 2.0, 3.0, etc. for the third octet.
256-192=64, 128, 192 for the fourth octet. For every valid subnet in the
third octet, we get four subnets in the fourth octet: 0, 64, 128, and 192.
- Broadcast for the 1.0 subnet is 1.63, since the
next subnet is 1.64. Broadcast for the 1.64 subnet is 1.127, since the
next subnet is 1.128. Broadcast for the 1.128 subnet is 1.191, since the
next subnet is 1.192. Broadcast for the 1.192 subnet is 1.255.
- The valid hosts are as follows:
|
Subnet |
0.64 |
0.128 |
0.192 |
1.0 |
1.64 |
1.128 |
1.192 |
2.0 |
|
first
host |
0.65 |
0.129 |
0.193 |
1.1 |
1.65 |
1.129 |
1.193 |
2.1 |
|
last host |
0.126 |
0.190 |
0.254 |
1.62 |
1.126 |
1.190 |
1.254 |
2.62 |
|
broadcast |
0.127 |
0.191 |
0.255 |
1.63 |
1.127 |
1.191 |
1.255 |
2.63 |
On this one, the 0 and 192 subnets are valid, since we are
using the third octet as well. The subnet range is 0.64 through 255.128. 0.0 is
not valid since no subnet bits are on. 255.192 is not
valid because then all subnet bits would be on.
Example 8: Class B network 255.255.255.224
- 211-2=2,046 subnets
- 25-2=30 hosts per subnet
- 256-255=1.0, 2.0, 3.0, etc. for the third octet.
256-224=32, 64, 96, 128, 160, 192 for the subnet value. (For every value
in the third octet, we get eight subnets in the fourth octet: 0, 32, 64,
96, 128, 160, 192, 224.)
- Broadcast for the 1.0 subnet is 1.63, since the
next subnet is 1.64. Broadcast for the 1.64 subnet is 1.127, since the
next subnet is 1.128. Broadcast for the 1.128 subnet is 1.191, since the
next subnet is 1.192. Broadcast for the 1.192 subnet is 1.255.
- The valid hosts are:
|
Subnet |
0.32 |
0.64 |
0.96 |
0.128 |
0.160 |
0.192 |
0.224 |
1.0 |
|
first
host |
0.33 |
0.65 |
0.97 |
0.129 |
0.161 |
0.193 |
0.225 |
1.1 |
|
last host |
0.62 |
0.94 |
0.126 |
0.158 |
0.190 |
0.222 |
0.254 |
1.30 |
|
broadcast |
0.63 |
0.95 |
0.127 |
1.159 |
0.191 |
0.223 |
0.255 |
1.31 |
For this subnet mask, the 0 and 224 subnets are valid as
long as not all subnet bits in the third octet are off or all subnet bits in
the fourth octet are on.
When would you use this valuable information? All the
time! For example, if you have a host configuration of 172.16.10.33
255.255.255.224, what subnet, broadcast address, and valid host range is this
host a member of? (We would solve this question with the information presented
above.)
256-224=32, 64
Bingo! In the fourth octet, the host address is 33. That
is between 32 and 64, so the host is in the 32 subnet, which has a broadcast
address of 63, and the valid host range is 33-62. Easy.
Just remember that the subnet is 10.32 because the third octet is part of the
subnet address.
Let's try a host configuration of 172.16.10.33
255.255.255.240. What subnet, broadcast address, and valid host range is this host a member of?
Since we did not go through this mask in this article,
you'll have to figure it out on your own. It is done the same way as all the
others.
256-240=16, 32, 48
Bingo! The host is in the 10.32 subnet, which has a
broadcast address of 10.47 and a valid host range of 10.33 through 10.46.
Let's keep going: Consider a host configuration of
172.16.10.33 255.255.255.248. What subnet, broadcast address, and valid host
range is this host a member of?
256-248=8, 16, 24, 32,
40
Bingo! The host is in the 10.32 subnet, which has a
broadcast address of 10.39 and valid host range of 10.33 through 10.38. Easy, huh?
One more: You have a host configuration of 172.16.10.17
255.255.255.252. What subnet, broadcast address, and valid host range is this host a member of?
256-252=4, 8, 12, 16,
20
Bingo! You have a subnet of 10.16, with a broadcast of
10.19 and valid host range of 10.17 through 10.18.
TCP/IP suite
The TCP/IP suite is composed of several protocols, as noted in the TCP/IP stack
model:
TCP/IP STACK MODEL
Application layer
- FTP (File Transfer Protocol)
- HTTP (Hypertext Transfer Protocol)
- SMTP (Simple Mail Transfer Protocol)
- Telnet
Transport
layer
- TCP (Transmission Control Protocol)
- UDP (User Datagram Protocol)
Internet
layer
- ARP (Address Resolution Protocol)
- RARP (Reverse Address Resolution Protocol)
- IP (Internet Protocol)
- ICMP (Internet Control Message Protocol)
- IGMP (Internet Group Membership Protocol)
- RIP (Routing Information Protocol)
Network
Access layer
- Physical Transmission Layer (Cat 5, etc.)
- Framing Protocols (Ethernet, etc.)
The Application layer
Let's start at the top. The Application layer runs its services via the layer
immediately below it—the Transport layer. In essence, it exploits TCP and UDP
to deliver its goods. The Application layer is no slouch, however, as it
functions to infiltrate and interact. DNS (Domain Name System) and FTP perform
at this level, as does HTTP, Telnet, SMTP, SNMP (Simple Network Management
Protocol), and a myriad of other applications. Windows Sockets operate here in
the Microsoft scheme.
The Transport layer
The Transport layer provides communication between host computers for data
delivery that's dependent on either of the two Transport protocols: TCP or UDP.
TCP is the antithesis of IP. It's like the yin to the yang of IP, whereas it
provides guaranteed delivery of its packets—but at a cost of speed.
Comparatively speaking, there's a bit of overhead as it goes through the steps
of establishing a connection—reducing a file into manageable packets and reconstructing
these packets at the recipient's end, and the "return receipt
required" or acknowledgement (ACK) that the packet was received in a
useable form. FTP and Telnet come into play here, but we'll discuss those
later.
UDP is like IP in that it doesn't guarantee delivery of packets, but it does
have very low overhead. No acknowledgement of receipt is required, no
retransmission, and so on. If you've used streaming media technology—RealNetworks' RealPlayer, for example—you've experienced
the best UDP has to offer. UDP is fast, but performance suffers because of
skips and gaps in the data transmissions.
The Internet layer
The Internet layer isn't only responsible for routing packets and datagrams, it's also responsible for letting the Network
Access layer know where to route them to. In order to do this, it utilizes ARP
to grab MAC (Media Access Control) addresses to deliver to and from and RARP to
provide delivery to diskless computers.
ICMP relays all information relating to bad delivery, problems, and errors to
the host computers. IGMP provides data to just about everyone willing to
listen—multicasting is the "shout-out" of the suite.
RIP takes care of routing across networks. It finds out how to deliver packets
to its recipient. IP addresses and routes packets to and from host computers.
It doesn't guarantee delivery; however, it will do whatever it can to deliver
its packets.
The Network Access layer
The Network Access layer is the equivalent of a loading dock, where the data
frames are put on the 10Base-T (or media of your choice) by token ring (or
Ethernet, etc.), and are also taken off.
TCP/IP tools and
utilities
TCP/IP is rather practical but it isn't fail-safe. On the upswing, there are
many tools and utilities available beyond simply surfing and grabbing pages off
the Internet via HTTP.
Essentially, TCP/IP tools and utilities can be broken into four groups:
Diagnostic, Data Transfer, Remote Execution, and Printing. Within each of these
are subsets of utilities specific to each. I'll explore some of the more common
ones.
Diagnostic utilities
Every good mechanic has a toolbox; if you're going to fix a problem, you need
to know at what root it lies in order to troubleshoot it. TCP/IP is no
exception.
PING
PING (Packet Internet Groper) is perhaps the simplest and most commonly used
diagnostic tool of all. Run at the command line (as all of these tools are),
or
PING Name.com
If successful, you'll get a reply. If not, you'll get the message "Request
timed out" for each packet that failed along the way. Several common
|
Table A |
|
|
-a |
Resolves
addresses to host names. |
|
-t |
PINGs a specific host until you tell it to quit. Referred to as
the " |
|
-n |
Specifies
the number of echo packets to send out (default 4). |
|
-l |
Indicates
the size of the echo packets (default 64 bytes). |
Here are some common
The most under-utilized aspect of
IPCONFIG
As you may have guessed, IPCONFIG is short for IP Configuration. It's almost
exclusively used in DHCP (Dynamic Host Configuration Protocol) networks. DHCP
is the way to manage and administer IP addressing among your clients on your
network.
IPCONFIG (and to an extent, its Windows 9x cousin, WINIPCFG) will provide the
vitals of a TCP/IP configuration:
 IP Address
 Subnet Mask
 Default Gateway
You can also utilize the switches shown in Table B, [where (x) is your
adapter].
|
Table B |
|
|
/all |
Displays
everything about your IP configuration. |
|
/release
(x) |
On a DHCP
network, lets go of its IP address lease, disabling
TCP/IP communications. |
|
/renew
(x) |
Again, on
a DHCP network, regains a dynamically assigned IP address lease. |
Here are some common IPCONFIG
switches.
On Windows 9x boxes, WINIPCFG will perform these functions
in a neat little GUI package.
ROUTE
ROUTE tells you everything you want to know about routes and routing at the
local level. Not only does it provide you with data to view, it also allows
route modification. Some of the most common switches are shown in Table C.
|
Table C |
|
|
command |
Add,
change, delete, and print. |
|
destination |
Specifies
the host's end. |
|
-f |
Deletes
gateway entries. |
|
gateway |
Specifies
gateway. |
|
MASK |
Displays
the network mask (255.255.255.255 by default). |
|
-p |
Forces a
persistent route. |
Here are some common ROUTE switches.
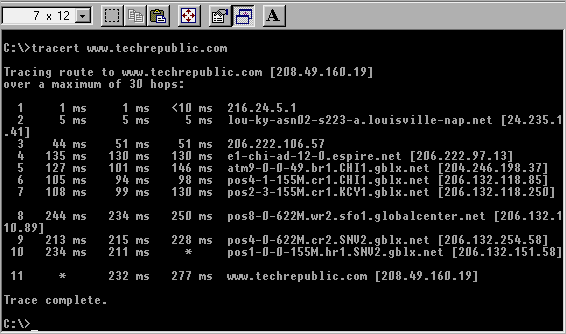
TRACERT
TRACERT is my personal favorite. As the name implies, it discovers, or TRACE ROUTEs the path from your local host to your destination
host. It helps designate failed or slow links, as well as provides information
about where all your packets travel on their way to a particular destination.
Common TRACERT commands are shown in Table D.
|
Table D |
|
|
-d |
If you
need fast tracing, use this switch to exclude the resolution of IP addresses
to host names. |
|
-h |
Followed
by your specified number, this switch provides routing information via the
amount of hops it takes to reach a particular destination. |
|
-w |
Waiting
time for replies. |
Here are some common TRACERT
switches.
ARP
The Address Resolution Protocol will resolve IP addresses to MAC addresses.
It's useful in discovering network configurations on the fly. Common ARP
switches are shown in Table E.
|
Table E |
|
|
-a, -g |
Displays
the cached entries of IP to MAC addresses; add the inet_addr
for a certain host. |
|
-d |
Deletes
the inet_addr specified in the ARP list. |
|
inet_addr |
Provides
the IP address. |
|
ether_addr |
Provides
the MAC address in hex. |
Here are some common ARP switches.
HOSTNAME
HOSTNAME provides your local host's name, which is useful to know if you're
going to
NETSTAT
NETSTAT provides Network (protocol) statistics and their current state. This
can encapsulate details for the following protocols: TCP, IP, ICMP, and UDP.
Several commands you can use for NETSTAT are shown in Table F.
|
Table F |
|
|
-a |
Displays
all connections and open ports. |
|
-n |
Same as
–a, but shows connections and open ports numerically. |
|
-p |
Displays
designated protocol information for either of the Transport layer protocols
(TCP, UDP). |
|
-s |
Displays
statistics for TCP, IP, UDP, and ICMP. |
|
-r |
Displays
active connections and routes. |
Here are some common NETSTAT
switches.
NBTSTAT
As with NETSTAT, NBTSTAT provides network protocol statistics; however, it will
also provide NetBIOS over TCP/IP statistics. It's also useful for updating the
LMHOSTS cache. Common NBTSTAT switches are shown in Table G.
|
Table G |
|
|
-a |
Provides
a remote computer's name table via its computer name. |
|
-A |
Provides
a remote computer's name table via its IP address. |
|
-n |
Provides
host's name table. |
|
-c |
Provides
IP address and name table of a remote cache. |
|
-r |
Provides
name resolution statistics of names broadcast or by WINS (only if WINS is
enabled). |
|
-R |
Purge and
reload of a remote cache name table; these are taken from the LMHOSTS file
(only if LMHOSTS lookup is enabled). |
Here are some common NBTSTAT
switches.
NSLOOKUP
NSLOOKUP (Name Server Lookup) roughly looks up entries from DNS databases. Table
H shows a limited list of common NSLOOKUP switches.
|
Table H |
|
|
option - |
Used to
specify commands, such as the ones below. |
|
finger |
Displays
remote host information. Very informative. |
|
root |
Takes you
to the domain name space's root server. |
|
server |
Switches
a specified DNS from the default server. |
|
ls |
Displays
DNS domain records. |
|
set |
Changes
settings for various NSLOOKUP commands. |
Here are some common NSLOOKUP
switches.
Data transfer tools
This is what networking is all about—the sharing of data. Of course, you have
to move data from point A to point B and back again. Throwing a floppy disk
across the office is not acceptable. Across a TCP/IP connection, FTP is the way
to go. FTP allows for the transfer of information when you either download it
from or upload it to a remote host. The data transfer commands are shown in Table
I.
|
Table I |
|
|
?, help |
Lists FTP
commands. |
|
ascii |
By
default, file transfer is set to this. |
|
binary |
Changes
file transfer to binary. |
|
dir |
Lists
files and subdirectories in a directory. |
|
cd |
Changes
directories. |
|
delete |
Deletes
files. |
|
get |
Retrieves
and copies files from a host to your local computer. |
|
put |
Copies/uploads
your file to the remote host. |
|
type |
Shows the
file transfer type. |
|
bye, quit |
Logs you
off from an FTP session. |
Here are some common data transfer
commands.
TFTP (Trivial File Transfer Protocol) is similar to FTP;
however, while FTP demands authentication from the user, TFTP does not. TFTP
simply transfers data.
Remote execution tools
In order to control or merely interact with a remote host, you'll need to work
from an interface. Telnet is perhaps the best-known and most widely used
protocol. Its flexibility can provide access across server ports. RSH (Remote
Shell) provides access to run commands on UNIX hosts. REXEC allows remote
execution on remote hosts.
Printing utilities
The commands shown in Table J are used primarily to interact with line
printers.
|
Table J |
|
|
LPR |
Line
Printer Remote: Prints at a remote host. |
|
LPD |
Line
Printer Daemon: The host handling LPR print jobs. Sends them out to the
device. |
|
LPQ |
Line
Printer Queue: Provides print queue information. |
Troubleshooting TCP/IP
Talainia Posey
The
TCP/IP protocol is the backbone of the Internet. It's also heavily used in wide
area networks. Unfortunately, due to the complexity of large networks, it can
be especially difficult to obtain an accurate diagnosis when problems occur. In
this article, I'll explain several techniques that you can use to troubleshoot
TCP/IP when things go wrong.
Why troubleshoot
TCP/IP?
So, why is troubleshooting TCP/IP such a big deal? TCP/IP isn't one of those
components that you can say is either working or not working. Instead, TCP/IP
may be partially functional, thus giving the illusion that it's working. This
situation is possible because TCP/IP consists of many subcomponents.
Some background
information
Before I go blazing gung-ho into the diagnostic procedure, it's important to
understand some basics about the way that TCP/IP works. Unlike most other
protocols, TCP/IP requires some configuration. This configuration may be
automatic (through a DHCP server) or manual.
The most basic parts of the TCP/IP configuration are the IP address and the
subnet mask. The IP address is a series of four numbers separated by periods.
An IP address looks something like this: 147.100.100.62. A portion of the
address contains the actual address that's assigned to the PC, while another
portion defines a number assigned to the network. If this idea seems strange to
you, imagine that you have a Web server. For users on the other side of the
world to access that Web server, they must know the general location (the
network number) before they can find the specific server within the network.
The portion of the address that makes up the network number is defined by the
subnet mask. The subnet mask also consists of four numbers separated by
periods, such as 255.255.0.0. A subnet mask like this one tells TCP/IP that two
of the numbers make up the network number (147.100) and the other two numbers
(100.62) are the computer's number. Keep in mind that this explanation is
simplified. In real life, subnets may divide individual networks into smaller
pieces. However, for the purposes of this article, you need only be familiar
with the basic concept.
Another configurable parameter in TCP/IP is the WINS settings. As you may know,
WINS is a service that provides NetBIOS name resolution on the local network.
The WINS fields enable you to enter the IP addresses of a primary and a backup
Windows NT Server that's running the WINS service on your network segment.
Like the WINS field, the DNS fields allow you to enter the IP addresses of a
primary and a backup Windows NT Server that's running the DNS service. DNS is
responsible for resolving domain names. For example, the name TECHREPUBLIC.COM
would be resolved through a DNS server.
Where do I begin?
Now that you have a basic understanding of some of the major portions of
TCP/IP, you may be puzzled as to where to begin the troubleshooting process.
When troubleshooting TCP/IP, I recommend starting close to home and working
outward. Basically, that means making sure that your own machine is functional,
testing your network in general, and then checking your Internet connection.
The local address
The first step in the troubleshooting process is to verify that your PC has a
valid IP address with which to work. As I mentioned earlier, most of the PCs on
a network can use either a static or dynamic IP address. To determine which
category your PC falls into, open Control Panel and double-click the Network
icon. When you see the Network properties sheet, select the copy of TCP/IP
that's bound to your network card and click the Properties button. When you do,
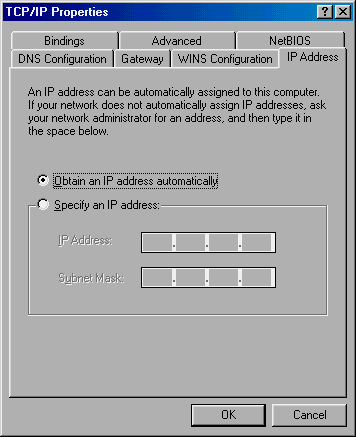
you'll see the TCP/IP properties sheet, as shown in Figure A.
|
Figure
A |
|
|
|
Determine
whether your PC is using a static or dynamic IP address. |
If the Specify An IP Address
radio button is selected, you should make sure that valid entries have been
made in the IP Address and Subnet Mask boxes. If, on the other hand, the Obtain
An IP Address Automatically radio button has been
selected, you must verify that you're receiving an IP address from a DHCP
server.
DHCP
DHCP stands for Dynamic Host Configuration Protocol, and it's a service that
can run on one or more Windows NT Servers within your organization. When the
Obtain An IP Address Automatically radio button is
selected, Windows will scan your network automatically for a DHCP server and
obtain an IP address. There are a couple of ways to find out if you're getting
an address from the DHCP server. The easiest method involves opening an MS-DOS
prompt window. If you're running Windows 9x, type WINIPCFG and press
[Enter]. When you do, you'll see a summary of your TCP/IP configuration as
Windows sees it. As you can see in Figure B, the IP Configuration dialog
box contains a drop-down list of your system's various adapters. Make sure that
you've selected the correct network adapter from the list before you jump to
any conclusions. It's easy to select a nonexistent dial-up adapter by mistake.
|
Figure
B |
|
|
|
Take care
to select the correct network adapter from the drop-down list. |
If you're using Windows NT, the command is slightly
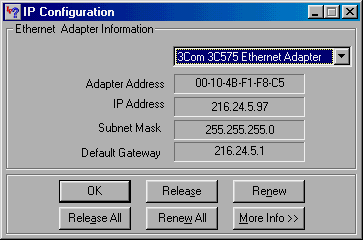
different. Windows NT users should type IPCONFIG. Doing so will display
a summary of the configuration information for all network devices, as shown in
Figure C.
|
Figure
C |
|
|
|
Windows NT
displays all TCP/IP configuration information. |
If you're trying to use a DHCP server to configure TCP/IP
but aren't having any luck, there are some things that you should check. First,
try reloading TCP/IP on your computer. It's possible that a file has become
corrupted. If that doesn't solve the problem, verify that the DHCP server is
running and that it's part of the same domain and subnet as your workstation.
Next, check to see whether your co-workers' PCs are functional. If they are
functional and rely on the DHCP server, it's a good bet that either the DHCP
server has run out of addresses or that there's a physical problem with your
machine, such as a bad network card or a disconnected network cable.
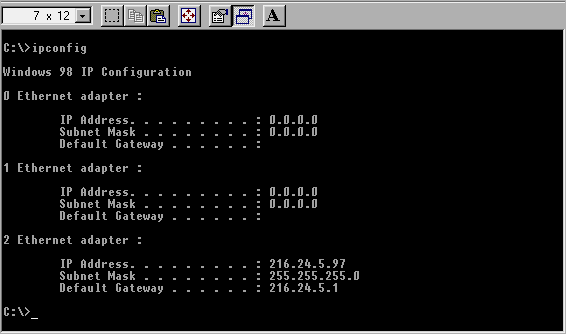
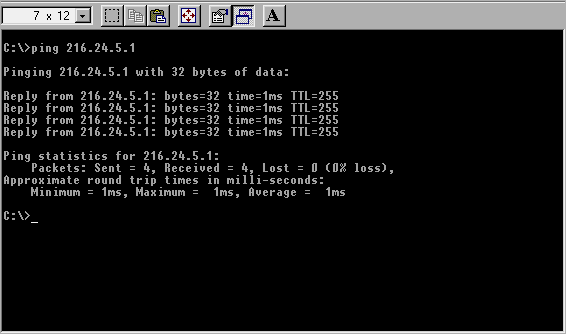
Go ping yourself
Once you've determined your IP address, you need to make sure that the basic
TCP/IP components are functional. To do so, open an MS-DOS prompt window and
try to ping yourself by typing ping and your IP address. For example,
you might type ping 147.100.100.62
Under normal circumstances, pinging should generate
four reply messages, as shown in Figure D. If you get an error message
instead, such as Destination Host Unreachable, there's a good chance
that Windows is messed up. If the ping is successful, it's time to move on to
the next phase of the troubleshooting process.
|
Figure
D |
|
|
|
The ping
should generate four reply messages. |
IP address conflicts
As you probably know, each PC on your network must have a unique IP address.
Duplicate addresses can cause all sorts of problems for your TCP/IP
environment. Fortunately, IP address conflicts aren't quite as difficult to
track down as most people think. If you suspect an IP address conflict, turn
off your PC. If your network uses static IP addresses, when you turn the PC
back on, you may receive a warning that the address is already in use. However,
if you don't get the warning or if you use dynamic IP addresses, just leave
your PC turned off for about an hour. Then, go to another PC and try to ping
your IP address. If the ping comes back with a reply, there's a good chance
that the address is in use by another PC. Double-check to make sure that your
PC is still turned off (since many newer PCs come with a "Wake on
LAN" feature). If your PC turns itself back on during the ping, try
unplugging it and running the test again.
If you determine that an IP conflict exists, the ARP command can help you
figure out which PC is the culprit. On some network configurations, the ARP
command can resolve the IP address to the computer's host name. Often, the host
name described the computer in some sort of detail. For example, a host name
might be MARY, or Accounting2, or Basement.
To check for a host name, type the command arp –a address where address is
the IP address that you want to test. If your network isn't configured to work
with host names, this command will return the physical ethernet
address of the machine.
The rest of the network
Once you've established with reasonable certainty that no IP address conflicts
exist, that there isn't a problem with Windows, and that your network
connection isn't unplugged, it's time to see if your computer can talk to the
rest of the LAN. One of the easiest ways of doing so is to log on. If the
computer logs on, that's a step in the right direction. Next, check Network
Neighborhood to see if any other computers show up. If they do, you're probably
okay on the local level. However, you should double-check to make sure that you
don't have any other protocols loaded. That way, you can be certain that it's
actually TCP/IP that's allowing you to see the other computers on your network.
WINS
If you can't see the other computers on your network, it may be due to a breakdown
in WINS. Check to make sure that TCP/IP is configured to use a WINS server.
Remember that you should check through WINIPCFG or IPCONFIG because they report
the configuration as Windows sees it, rather than simply regurgitating the
information that you've entered.
If your WINS entries look fine, check for more obvious problems like
disconnected cables or bad network cards. If the physical hardware checks out,
try pinging your WINS server, first by IP address and then by name. You don't
have to be logged on to the domain for it to work. An example would be if you
had a WINS server named Animal with an address of 147.100.100.28. First, try
pinging 147.100.100.28. If the ping is successful, you've established that
TCP/IP is definitely functional on your PC and that the physical link between
your PC and the WINS server is good. Next, try pinging
the WINS server by name, such as ping Animal. If this ping is
successful, it means that the WINS server is functional and that your PC is
using it correctly. Obviously, if you can ping the WINS server by number but
not by name, there's a breakdown in the basic WINS service functionality.
The Internet
If everything so far has checked out, you're well on your way to solving the
problem. The next step is to examine your Internet or wide area network (WAN)
connectivity. Doing so uses the same basic principle as testing your local
network. The main difference is that you'll be testing Domain Name Server (DNS)
functionality rather than WINS functionality. The DNS is responsible for
resolving domain names like www.techrepublic.com.
To test your DNS, open an MS-DOS prompt window and try to ping a favorite
Internet site by name. For example, try typing ping www.techrepublic.com
If the ping returns, then your DNS is working fine. If
it doesn't return, try pinging another site, just to
make sure that the first site you pinged wasn't down. If neither site generates
a return, try pinging by the site's IP address. For example, to test your link
to the TechRepublic Web site, type ping
208.49.160.19
If that ping returns, then there's a breakdown in your
DNS service. Try pinging your DNS server to make sure
that it's available. If it's available but isn't functioning, try attaching to
a different DNS server until you can fix your primary DNS server.
Is the host available?
If a numerical ping won't work, there are several possible causes. For example,
your local router could be malfunctioning, the site that you're trying to
access could be down, or a router somewhere on the Internet could be
malfunctioning.
To find the culprit, try using Tracert (
|
Figure
E |
|
|
|
Tracert can help you to find problems on the Internet. |
IP routing in 40 short steps
Todd Lammle
This article will zoom in on the principle of moving packets of data from
one network to another network using a router and the IP protocol. This is
called routing, and I'm going to demonstrate an IP routing example in 40 steps.
Why 40? Well, I really could give it to you in 10 steps or so, but that would
be more of a summarized approach. And since I really want you to thoroughly
understand this process, I'm going to cover the
details of how a packet is actually handled when it's sent through an internetwork.
Because we're taking an in-depth approach here, you'll find it helpful to be
familiar with the following:
- IP addressing and subnetting
- The difference between a router and a switch
- How collision and broadcast domains work within
an internetwork
IP
addressing, subnetting, and IP routing are very
important fundamentals; once you have a good grasp on them you can move on to
exploring more advanced, really exciting subjects like supernetting
and Variable Length Subnet Masking (VLSM)!
Move that data!
Okay, you know routers are hardware devices that employ software to perform the
task of routing packets throughout an internetwork,
and you know that routing is the term used to describe the process of taking a
packet of data from a device on one network and switching it through that
router over to another device on a different network—packet distribution and
delivery. So if your network has no routers, you're not routing.
|
Figure
A |
|
|
|
Did you
notice that a LAN and two WANs are connected to the 2600A router? |
Figure A highlights the routing raison d'etre: to make it possible to connect multiple networks,
thereby creating an internetwork so that all hosts
within that internetwork can communicate with each
other by sending and receiving data.
Now take a closer look at Figure A so we can go
step-by-step through the IP routing process. Let's begin by pretending that HostA wants to send a ping request (packet internet groper)
to HostB.
By looking at the IP networks and addresses in the figure,
we can see that HostA is on the 192.168.10.32 network
and that the /27 is a subnet block of 32. What this tells us is that our valid
hosts are 33-62. Also, notice that HostA's IP address
is 192.168.10.34 with a configured default gateway of 192.168.10.33.
HostB is on the 192.168.10.96 subnet and it has an IP address of
192.168.10.98 with a configured default gateway of 192.168.10.97. It's very
important to make sure that a host's default gateway is configured correctly
because it's used to tell the host how to send packets out of the local
network.
Okay, that said, let's type a ping request to
192.168.10.98 from HostA at the command prompt and
follow it through from beginning to end. Here's what happens, starting at HostA (these are our 40 steps to IP routing):
- Internet Control Message Protocol (ICMP) creates an echo request payload (which is just the alphabet forward and backwards).
- ICMP hands that payload to IP, which then
creates a packet. At a minimum, this packet contains an IP source address,
an IP destination address, and a protocol field with 01h. All of that
tells the receiving host whom to hand the payload to—in this example,
ICMP.
- Once the packet is created, IP works with the
Address Resolution Protocol (ARP) to determine whether the destination IP
address is on the local network or on a remote one.
- Since this is a remote request, the packet needs
to be sent to the default gateway. The registry in Windows is parsed to
find the configured default gateway.
- The default gateway of host 192.168.10.34 is
192.168.10.33. To be able to send this packet to the default gateway, the
hardware address of the router's interface Ethernet1 (configured with the
IP address of 192.168.10.33) must be known. Why? So the packet can be handed
down to the Data Link Layer, framed, and sent to the router's interface
for the 192.168.10.32 network.
- Now, the ARP cache is checked to see if the IP
address of the default gateway has been already resolved to a hardware
address. If it has, the packet is then free to be handed to the Data Link
Layer for framing. (The hardware destination address is also handed down
with that packet.)
- If the hardware address isn't already in the ARP
cache of the host, an ARP broadcast will be sent out onto the local network
to search for the hardware address of 192.168.10.33. The router will
respond to the request and provide the hardware address of Ethernet1, and
the host will cache this address. The 2500A router will also cache the
hardware address of HostA in the ARP cache.
- Once the packet and destination hardware address
are handed to the Data Link Layer, the LAN driver is used to provide media
access via the type of LAN being used. (In this example, it's Ethernet.) A
frame is then generated, encapsulating the packet with control
information. Within that frame are the hardware destination and source
address, plus an Ethernet-Type field that describes the Network Layer
protocol that handed the packet to the Data Link Layer (in this case, IP).
At the end of the frame is the Frame Check Sequence (FCS) field, which
houses the answers to the Cyclic Redundancy Check (CRC).
- Once the frame is completed, the frame is handed
down to the Physical Layer to be put on the physical medium (in this
example, twisted-pair wire), one bit at a time.
- Every device in the collision domain receives
these bits and builds the frame. They each run a CRC and check the answer
in the FCS field. If the answers don't match, the frame is discarded. If
the CRC matches (in this example, it is the router's interface Ethernet1),
then the hardware destination address is checked to see if it matches too.
If it's a match, then the Ethernet-Type field is checked to find the
protocol used at the Network Layer.
- The packet is pulled from the frame and the
frame is discarded. The packet is handed to the protocol listed in the
Ethernet-Type field, meaning it's given to IP.
- IP receives the packet and checks the IP
destination address. Since the packet's destination address doesn't match
any of the addresses configured on the receiving router itself, the router
will look up the destination IP network address in its routing table.
- The routing table must have an entry for the
network 192.168.10.96 or the packet will be discarded immediately and an
ICMP message will be sent back to the originating device with a
Destination Network Unavailable message.
- If the router does find an entry for the
destination network in its table, the packet will be switched to the exit
interface—in this example, interface serial 0.
- Serial interfaces don't use Ethernet framing
techniques, but by default, Cisco routers use something called High-Level
Data Link Control (HDLC) to frame the packet. When serial interfaces are
used, though, it's not called framing; it's known as "encapsulating."
And because this is a point-to-point circuit, hardware addresses aren't
used or needed. Instead, HDLC encapsulation is sent out one bit at a time
to the next router.
- Serial 0/0 on 2600A then extracts the packet
from the HDLC encapsulation and checks the IP destination address. Since
the IP addresses of the different router interfaces do not match, the
router will check its routing to determine whether it knows how to get the
packet over to the destination network.
- The routing table will show that to get to
network 192.168.10.96, it must use exit interface FastEthernet
0/0 so the packet is switched to interface FastEthernet
0/0.
- The FastEthernet
interface has the packet in the buffers and needs to send the packet to HostB, or IP address 192.168.10.98, but the hardware
address must be known in order to deliver the packet to the correct host.
The router checks the ARP cache, and if no match is found, an ARP
broadcast is sent out interface FastEthernet
0/0.
- HostB will respond with its hardware
address, and the packet and destination hardware address are both sent to
the Data Link Layer for framing.
- The Data Link Layer will create a frame with the
destination and source hardware address, Ethernet-Type field, and a FCS
field at the end of the frame. The frame is handed to the Physical Layer
to be sent out on the physical medium one bit at a time.
- HostB receives the frame and
immediately runs a CRC. If the answer matches what's in the FCS field, the
hardware destination address is then checked. If it finds a match, the
Ethernet-Type field is then checked to determine where the packet should
be received on the Network Layer.
- At the Network Layer, IP gets the packet and
checks the IP destination address. Since there's finally a match made, the
protocol field is checked to find out to whom the payload should be given.
- The payload is handed to ICMP, which understands
that this is an echo request. ICMP responds to this by immediately
discarding the packet and generating a new payload as an echo reply.
- A packet is then created including the source
and destination address, protocol field, and payload.
- ARP then checks to see if the destination IP
address is a local device on the local LAN or if it's a device on a remote
network. Since the destination device is on a remote network, the packet
needs to be sent to the default gateway.
- The default gateway address is found in the
registry of the Windows device, and the ARP cache is checked to see if the
hardware address has already been resolved from an IP address.
- Once the hardware address of the default gateway
is found, the packet and destination hardware address are handed down to
the Data Link Layer for framing.
- The Data Link Layer frames the packet of
information and includes the following in the header: the destination and
source hardware address, Ethernet-Type field with IP in it, and the FCS
field with the CRC answer in tow.
- The frame is now handed down to the Physical
Layer (of the OSI model) to be sent out over the network medium one bit at
a time.
- The router's FastEthernet
0/0 interface will receive the bits and build a frame. The CRC is run, and
the FCS field is checked to make sure the answers match.
- Once the CRC is found to be okay, the hardware
destination address is checked. Since the router's interface is a match,
the packet is pulled from the frame and the Ethernet-Type field is checked
to see what protocol at the Network Layer the packet should be delivered
to.
- That's determined to be IP, so it gets the
packet. IP runs a CRC check on the IP header first and then checks the
destination IP address. (Note: IP does not run a complete CRC like the
Data Link Layer—it only checks the header for errors.) Since the IP
destination address doesn't match any of the router's interfaces, the
routing table is checked to see if it has a route to 192.168.10.32. If it
doesn't have a route over to the 32 network, the packet will be discarded
immediately. (This is the source point of confusion for a lot of
administrators. When a ping fails, most people think the packet never
reached the destination host. But as we see here, that's not always the
case! All it takes is for just one of the remote routers to be lacking a
route back to the originating host's network and POOF! The packet is
dropped on the return trip, not en route to the host.)
- But Router 2600A does know how to get to network
192.168.10.32—the exit interface is serial 0/0—so the packet is switched
to serial interface 0/0.
- The serial interface builds an HDLC
encapsulation and sends the packet inside an HDLC encapsulation method out
interface 0/0, one bit at a time, to the 2500A router. The 2500A router
receives the HDLC encapsulation and hands over the packet to IP.
- IP checks the destination address, and since no
interface on the router matches, the routing table is checked for a path
to network 192.168.10.32.
- The routing table tells IP that the path to
network 192.168.10.32 is out interface Ethernet1, so over it goes—the
packet is switched to interface Ethernet1.
- The hardware address must first be found in
order to send the packet to the destination IP address of 192.168.10.34,
and the ARP cache is checked for that first. Since the address is in the
ARP cache, the packet and the destination hardware address are sent to the
Data Link Layer to be framed.
- The frame adds the hardware source and
destination address and the Ethernet-Type field, and puts the CRC answer
in the FCS field.
- The frame is then given to the Physical Layer to
be sent out onto the local network, one bit at a time.
- The destination host receives the frame, runs a
CRC, checks the destination hardware address, and then looks in the
Ethernet-Type field to find who to hand the packet to. IP, at the Network
Layer, is the designated receiver, and after the packet is handed to IP at
the Network Layer, it checks the protocol field for further direction. IP
finds instructions to give the payload to ICMP, and ICMP determines the
packet to be an ICMP echo reply. It acknowledges that it has received the
reply by sending an exclamation point (!) to the user interface. ICMP will
then attempt to send four more echo requests to the destination host.
|
Only
one ping? |
|
Five
pings are sent by default, but I don't think we need to go there! For those
individuals in the audience who want this article to describe the process
exactly as it actually happens in the real world, just start back at step one
and read through to number 40 four more times! |
Conclusion
The beauty of IP routing is that no matter how many more routes we might decide
to put into this example, the process would never change! The packet is just
sent from hop to hop until it reaches the destination network.
Remember to keep these important points in mind:
- Some things never change, and this includes packets.
They never change in any way; they are only encapsulated in control
information to enable them to be sent from one router to another.
- Routers are impersonal; they do not keep host addresses
in their routing tables. Routers only care about networks and the best
path to each one.
- Each and every hardware address is unique. These are
what devices use to find a unique host on a local network.